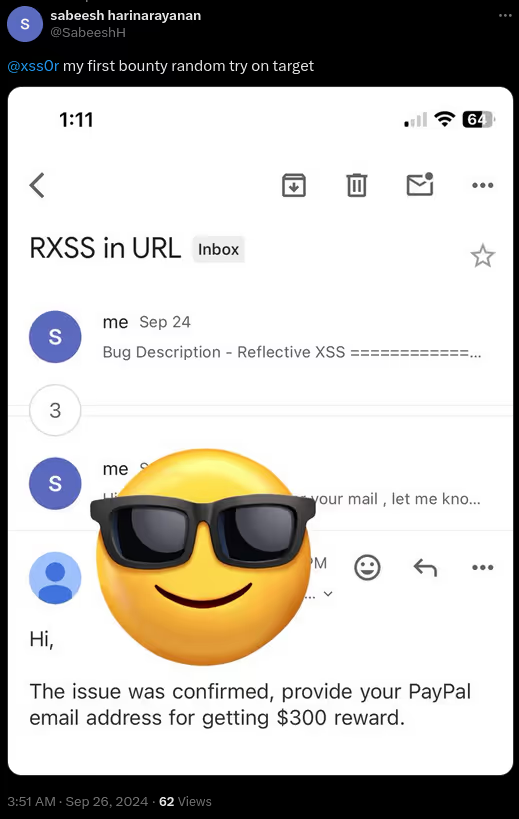
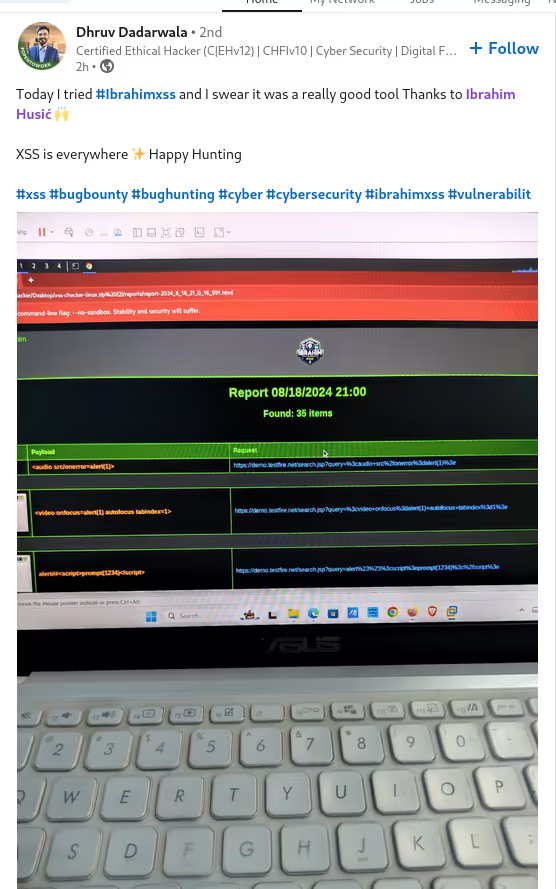
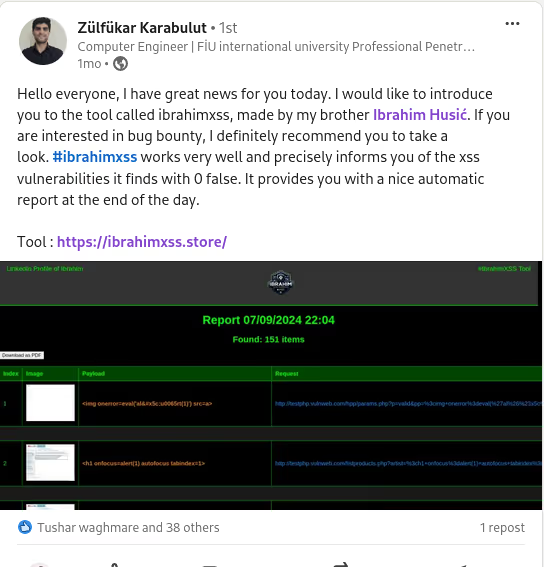
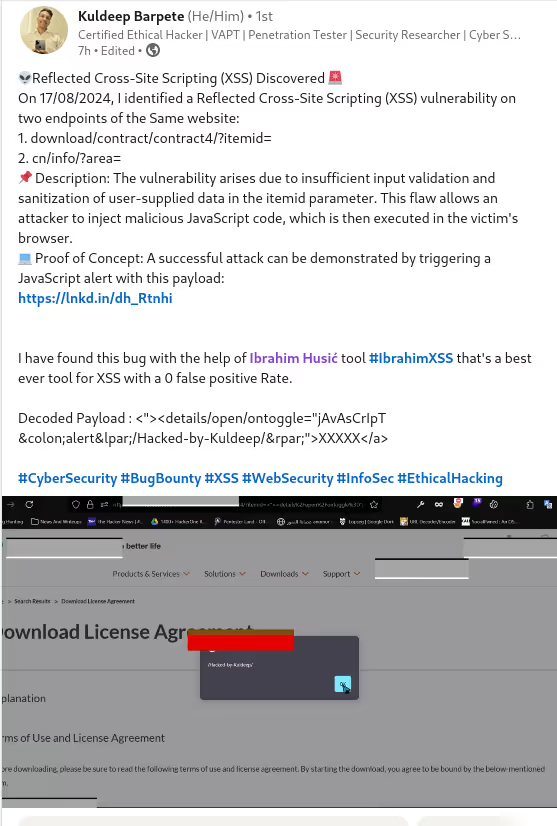
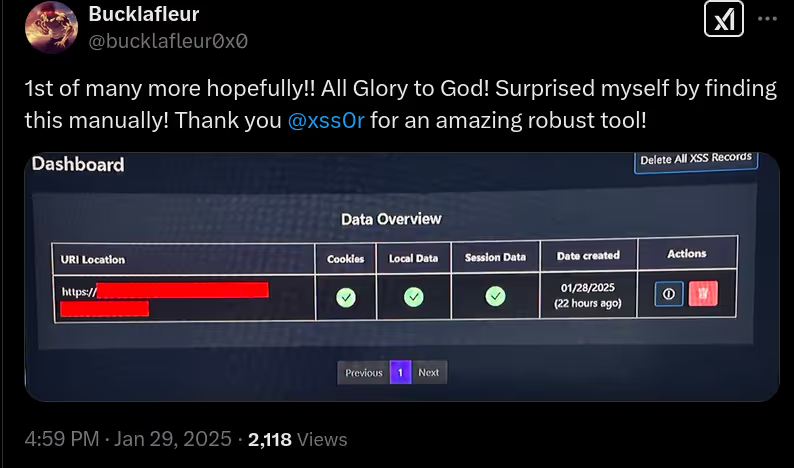
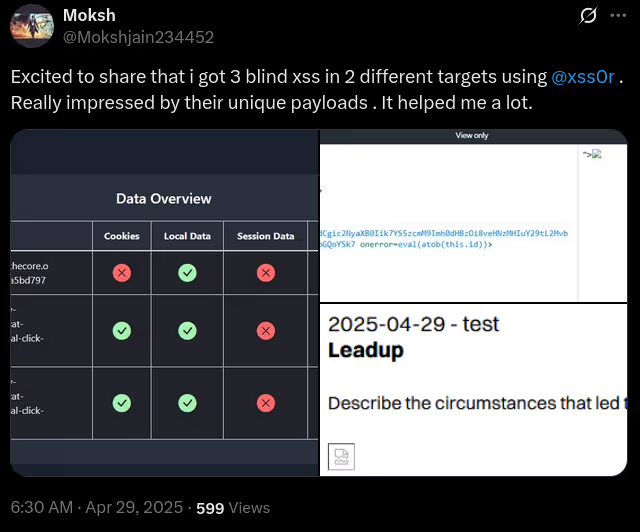
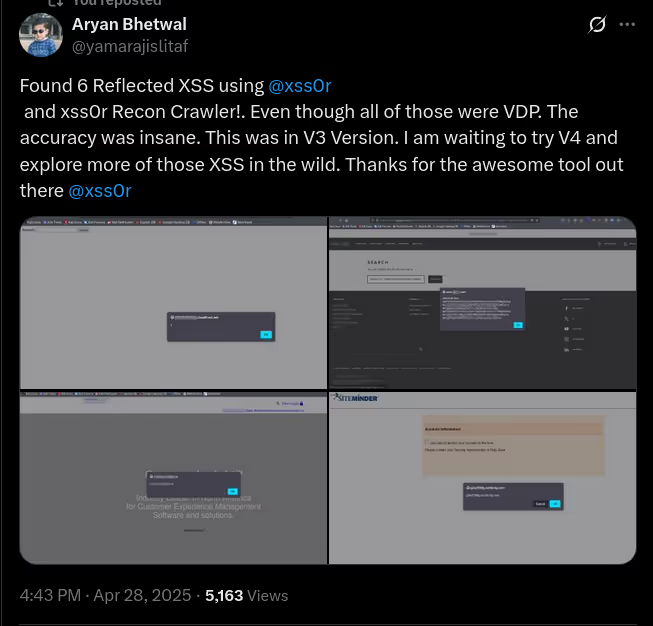
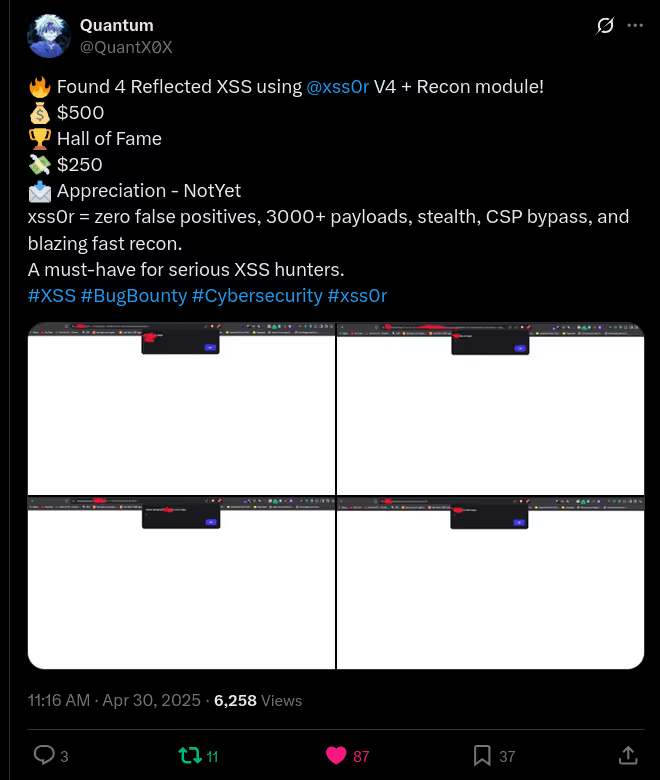
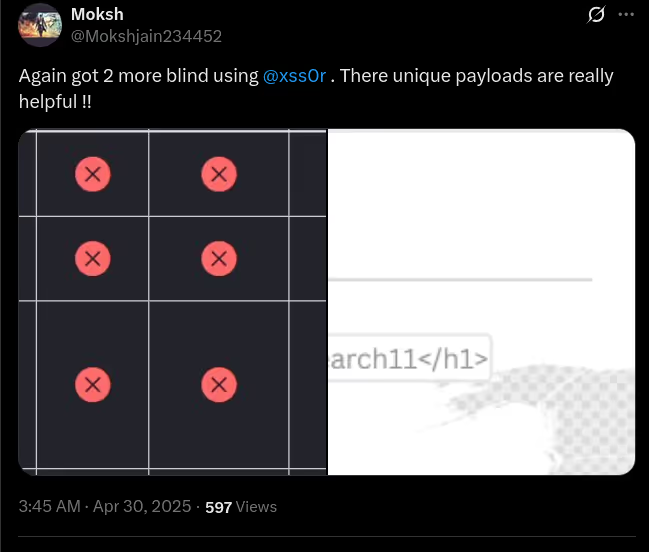
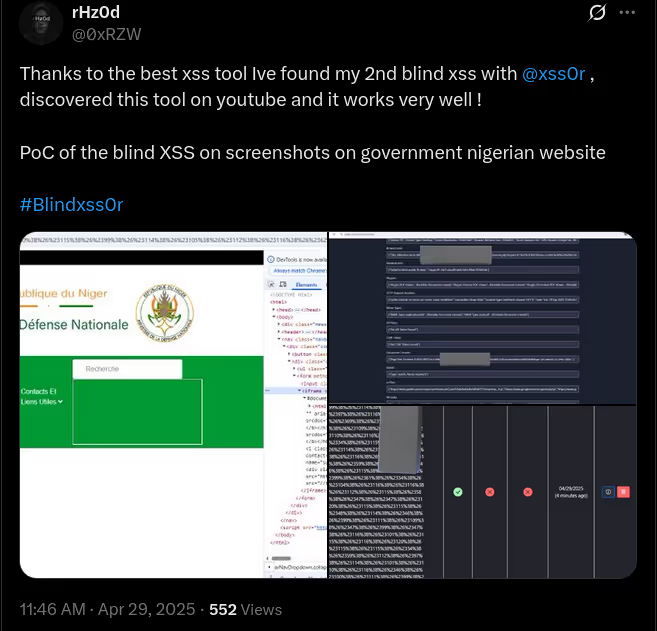
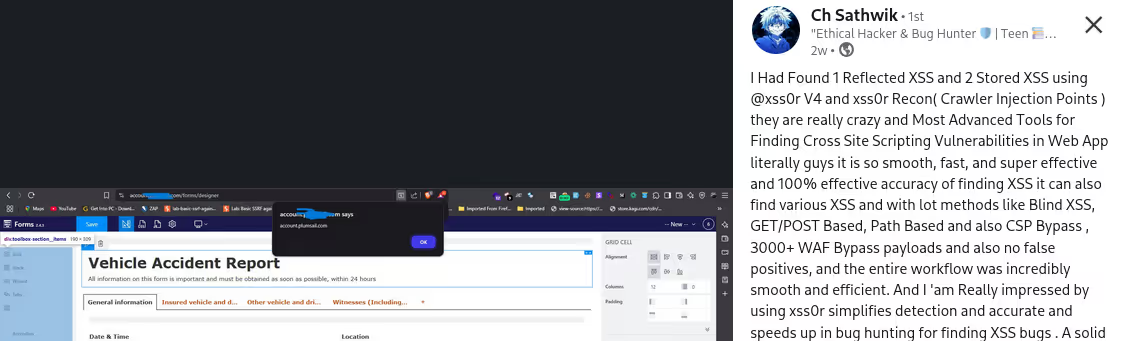
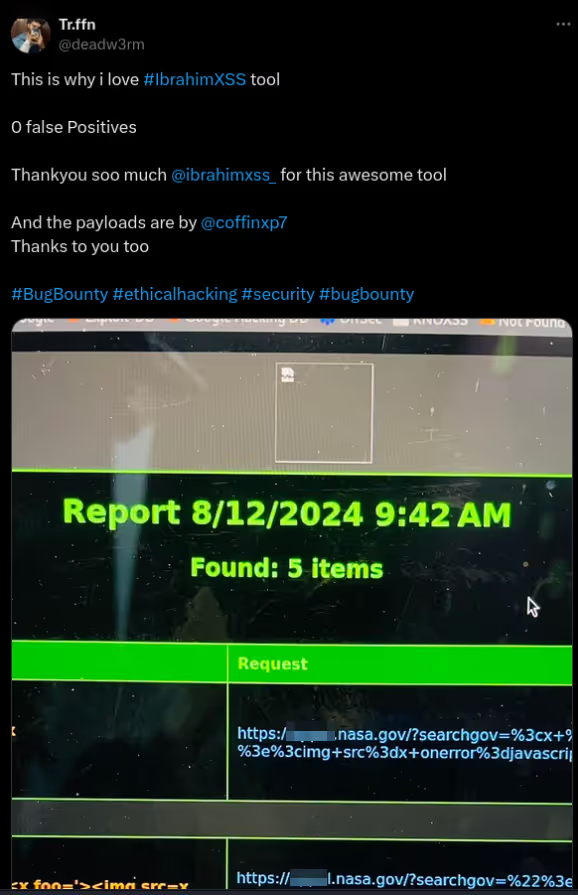
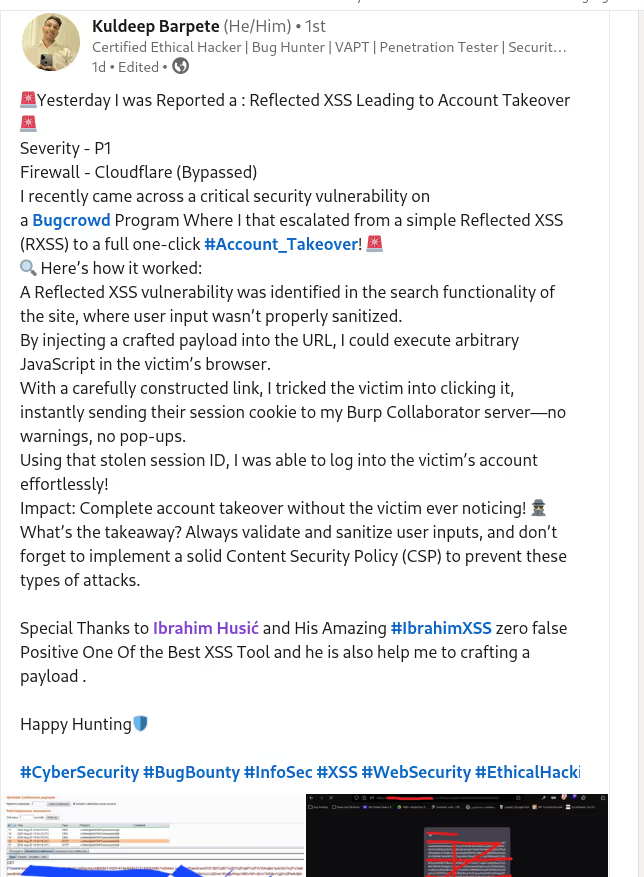
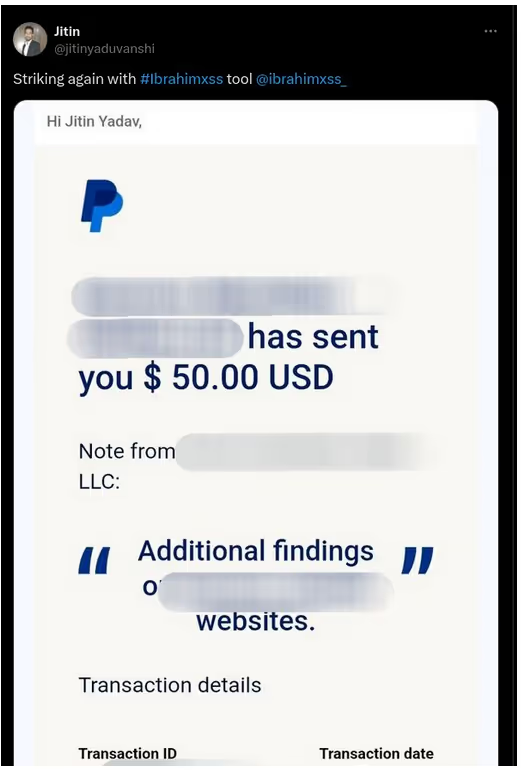
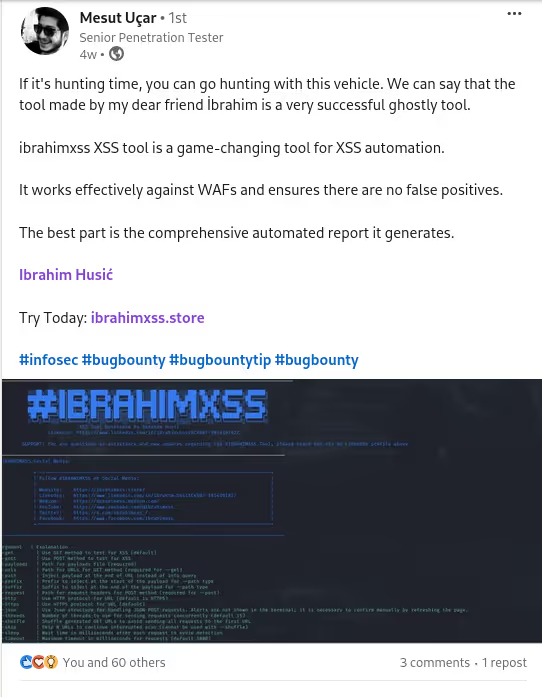
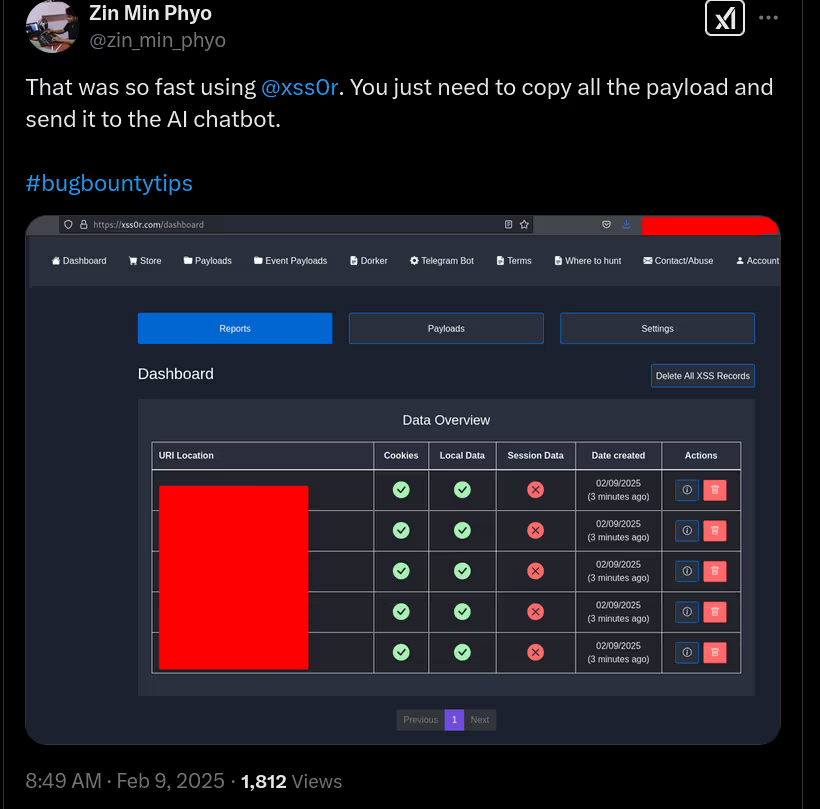
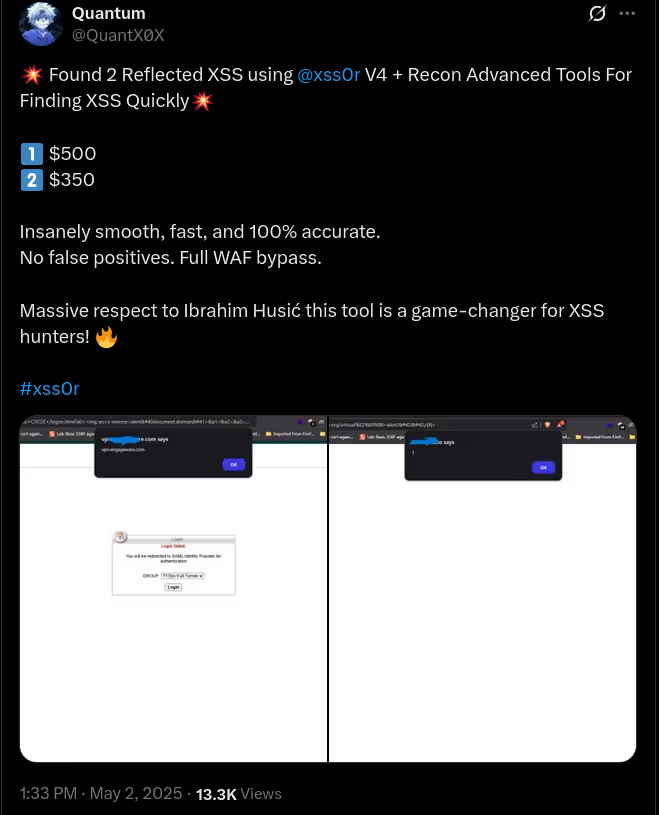
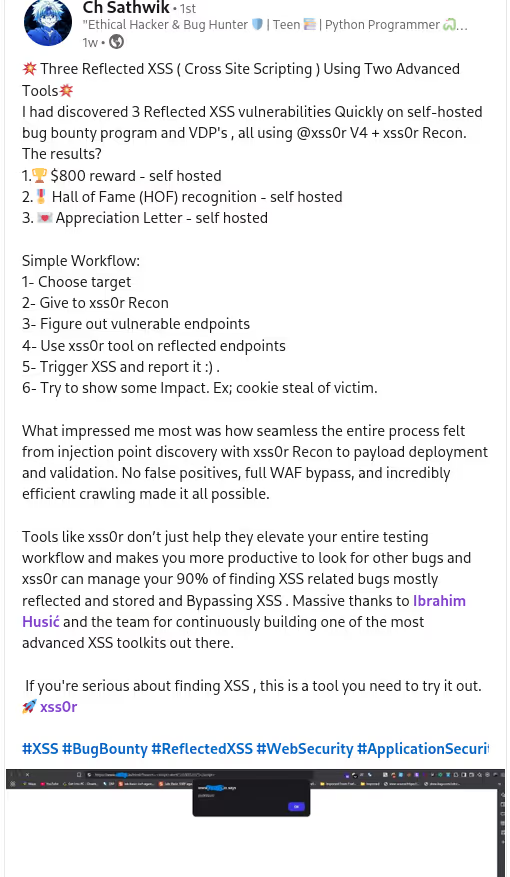
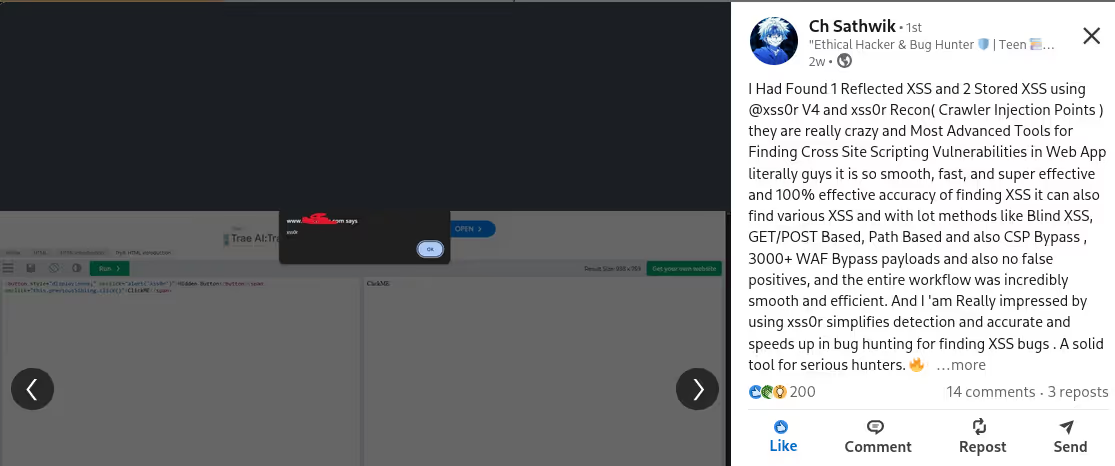
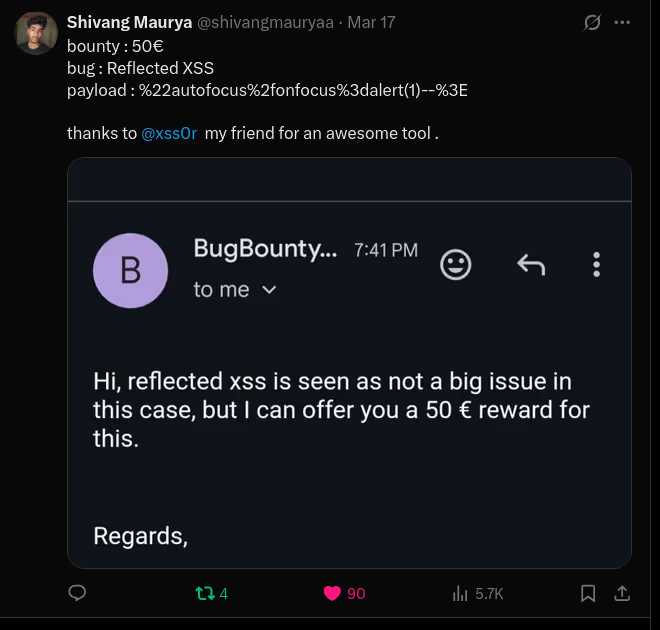
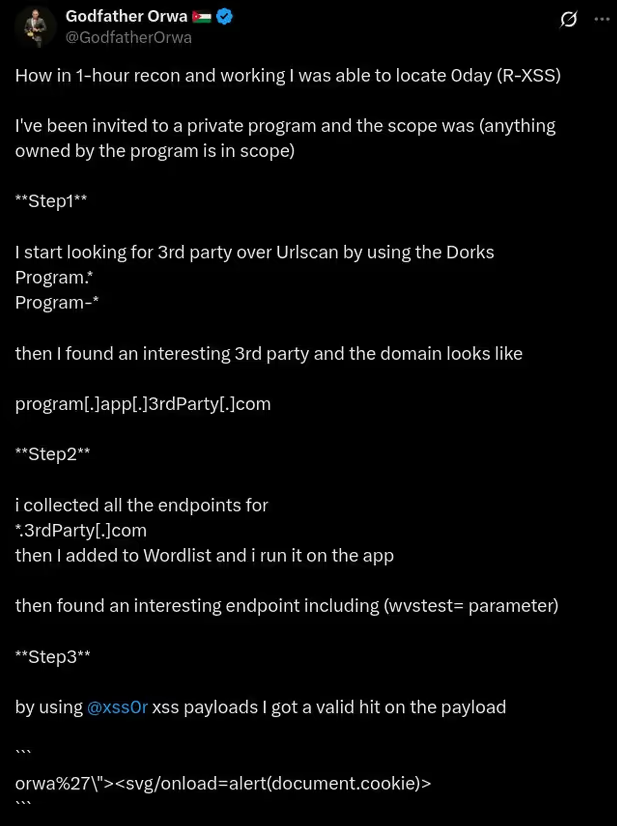
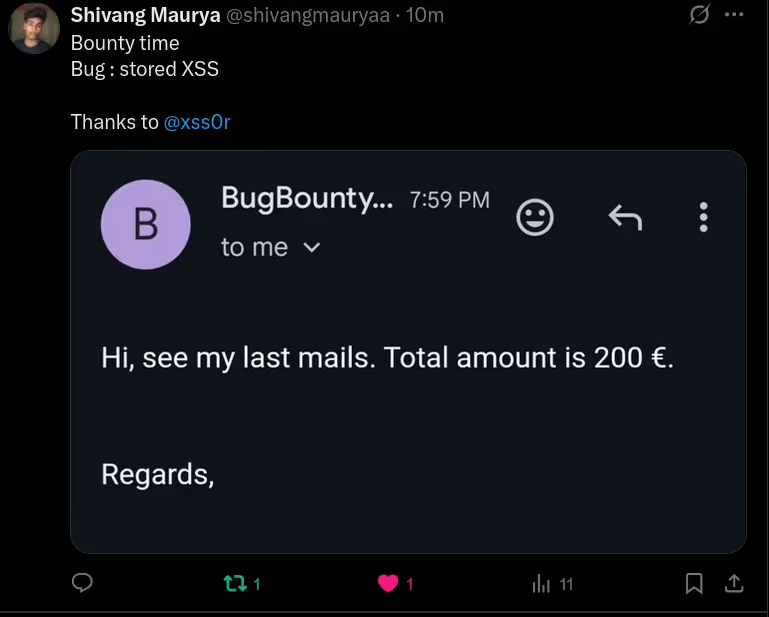
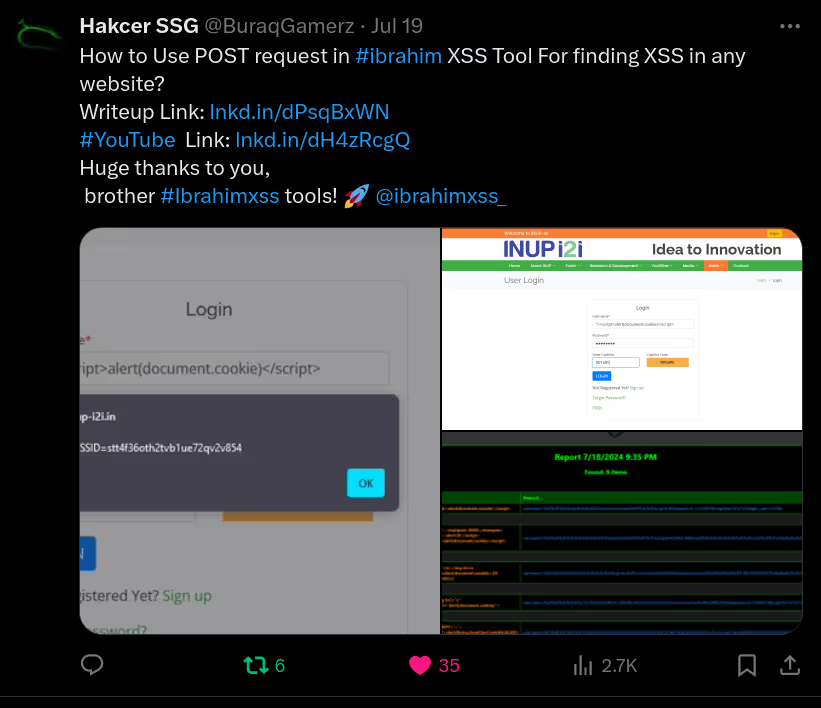
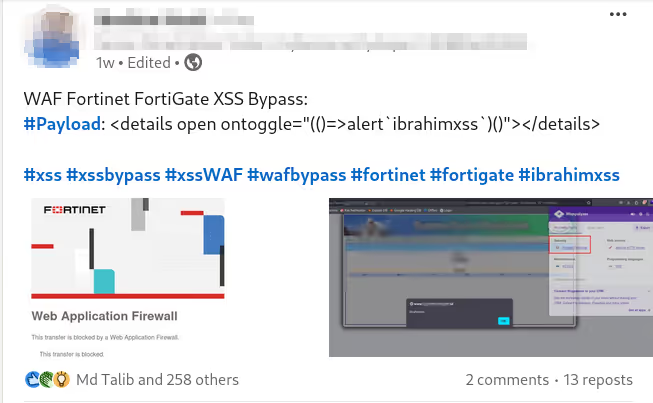
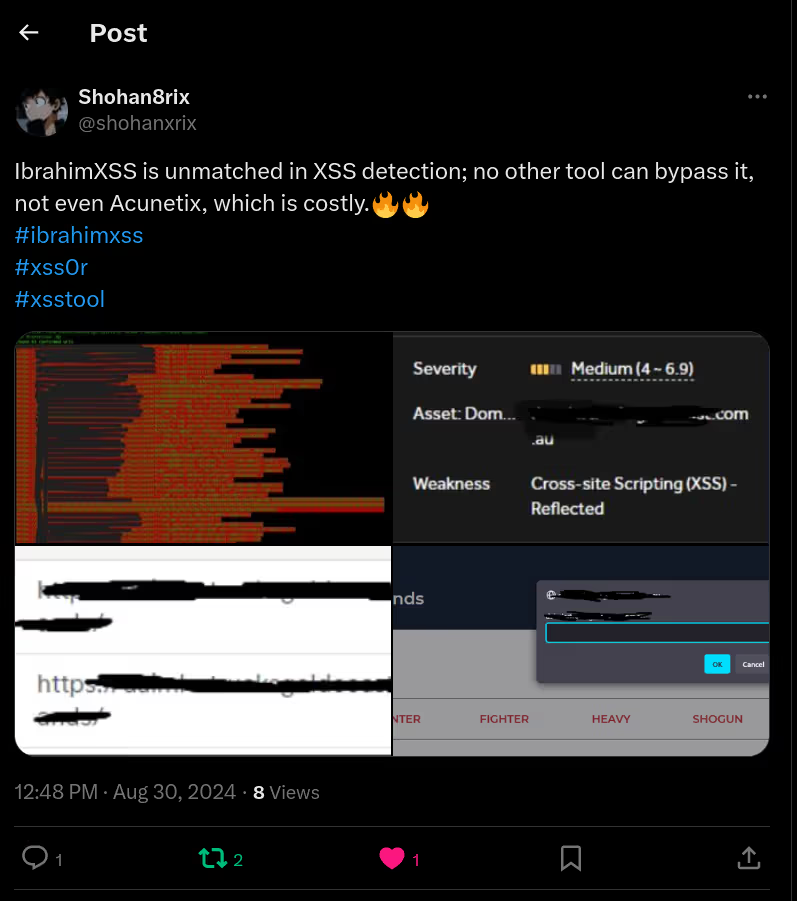
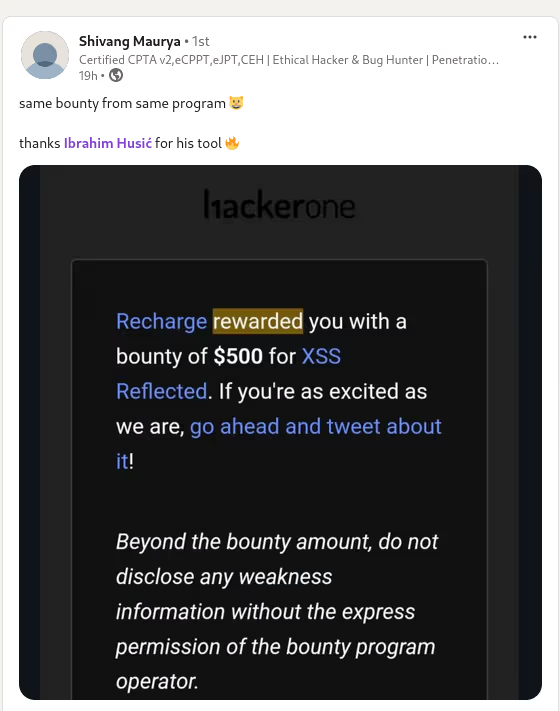
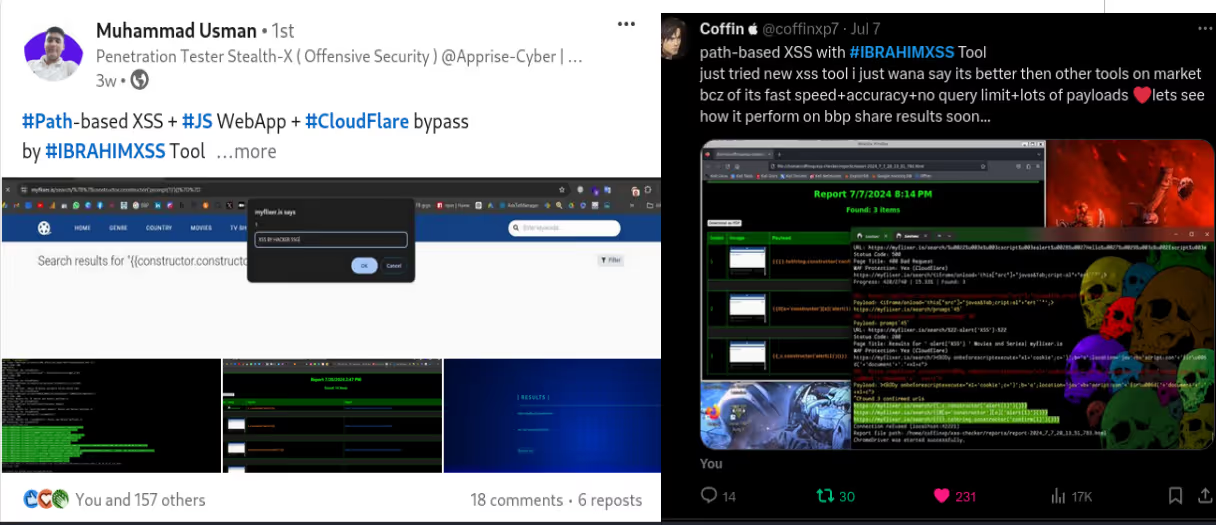
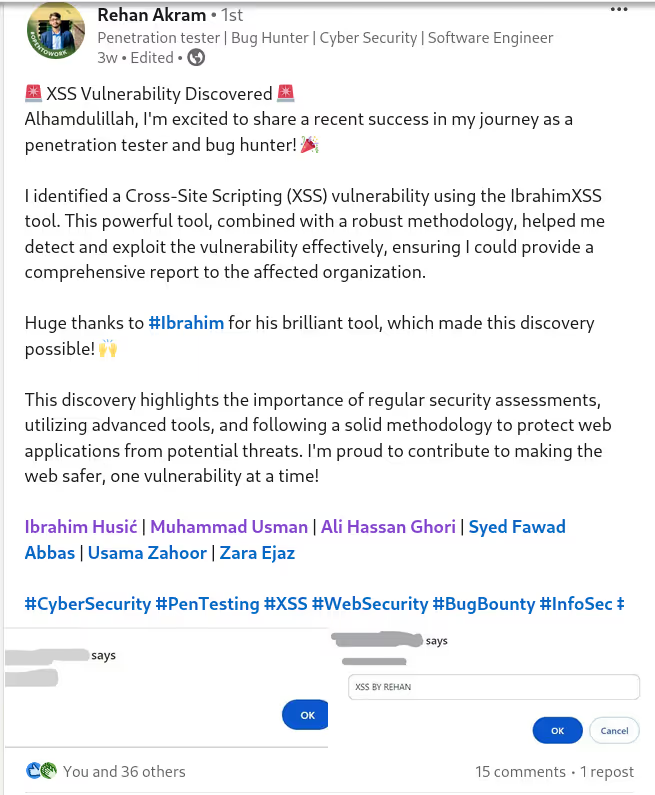
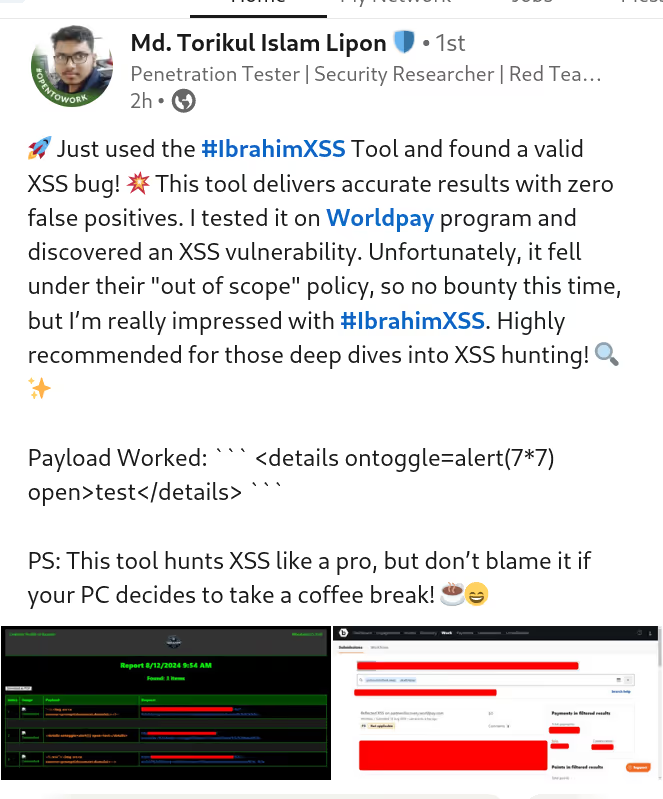
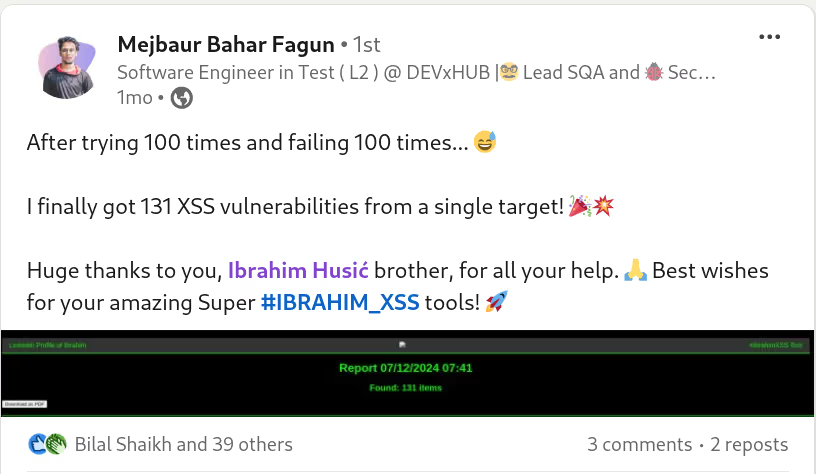
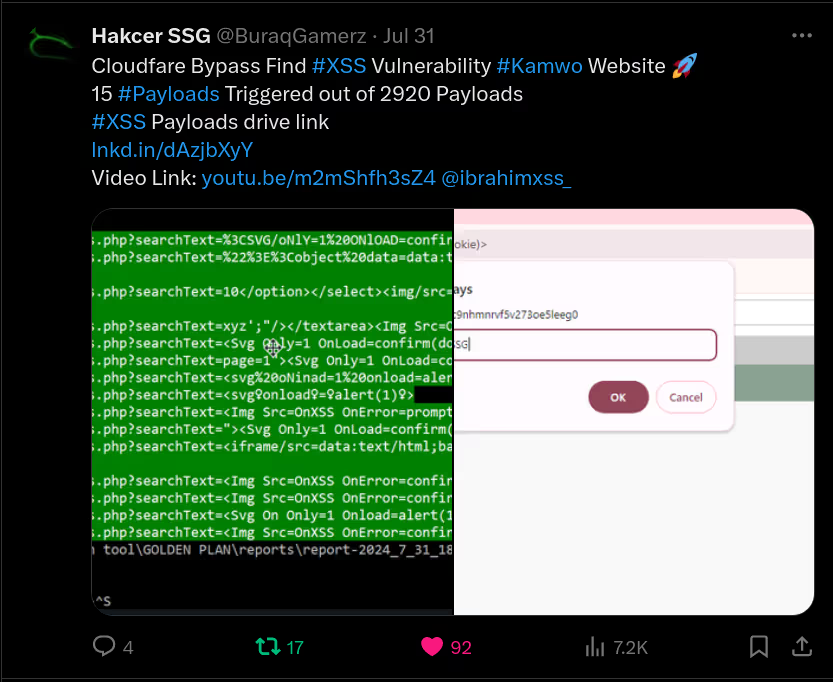
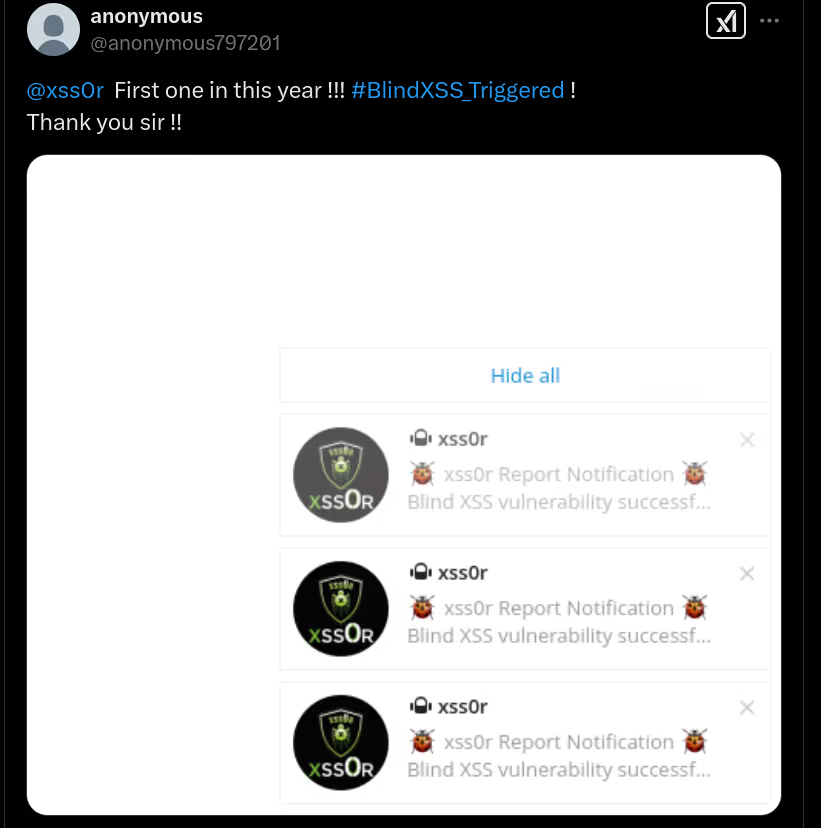
The BUSINESS PLAN is crafted for professionals and organizations requiring robust web security solutions. This plan offers advanced features such as GET, POST, and PATH request analysis, support for JSON WebApps, and Suffix & Prefix customization. With unlimited speed, access to private xss0r payloads, ClickMe Private Payloads, and comprehensive WAF bypass capabilities, it's designed for tackling complex vulnerabilities. Enjoy 24/7 technical support, cookie support for authenticated applications, and receive 2 free licenses. The BUSINESS PLAN provides all the tools needed for top-tier web security testing, making it an excellent choice for companies and clients focused on achieving strong protection.
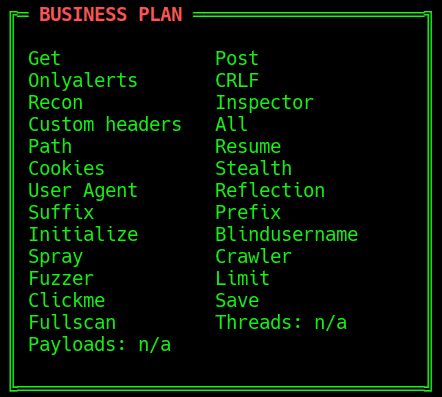
Complete Features Overview
✅Get / Post:
Run extensive XSS &vulnerability scans using both GET and POST methods.
✅ Onlyalerts:
Show only triggered alertsin the output, keeping logs clear and focused.
✅ Recon:
Full reconnaissance: domainenumeration, crawling, smart URL discovery.
✅ Custom Headers:
Use --headersto inject custom HTTP headers into requests.
✅ Path:
Inject payloads directly into URLpath segments.
✅ Cookies & Initialize:
Load cookiesand initialize sessions for authenticated scanning.
✅ User Agent:
Customize the User-Agentstring for stealth or advanced testing.
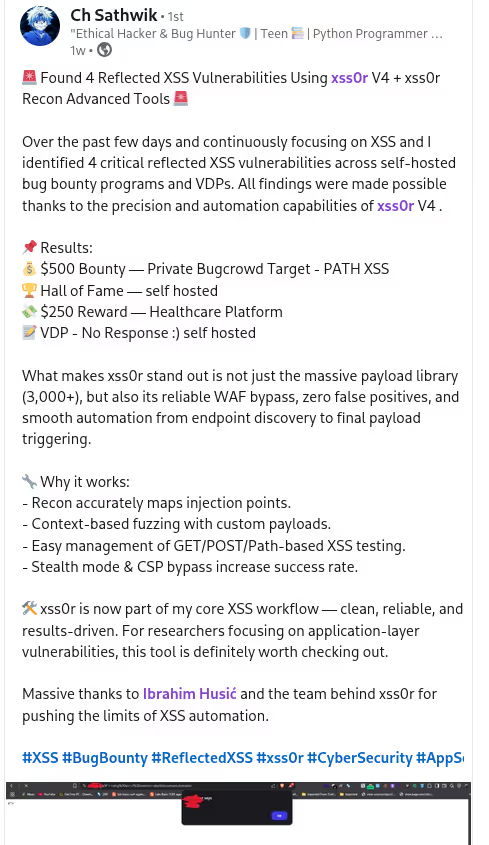
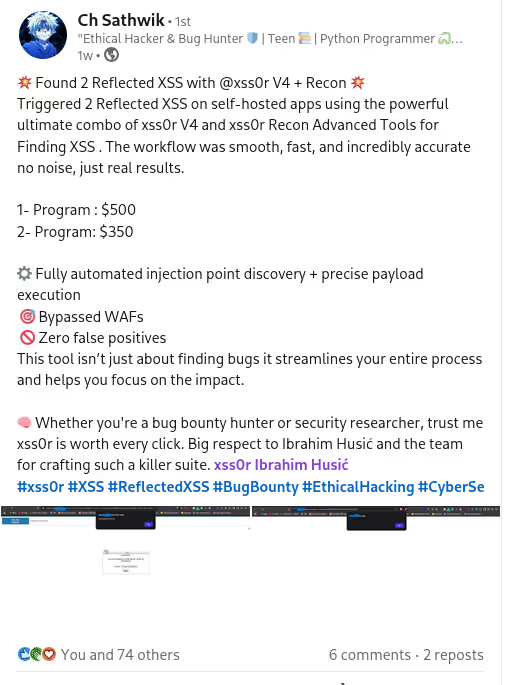
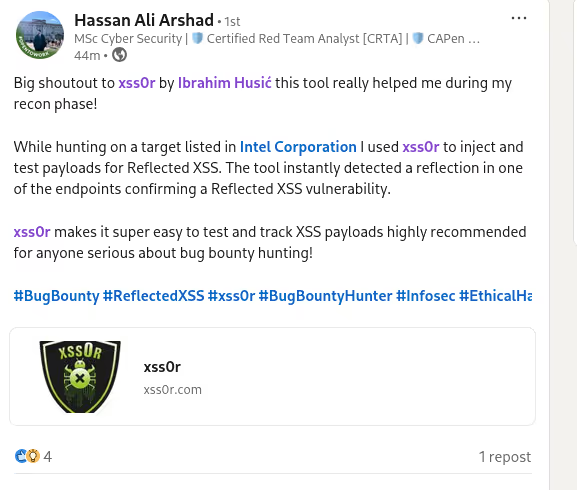
✅ Reflection:
Detect reflected parametersto pinpoint XSS-prone inputs.
✅ Suffix / Prefix:
Prepend or appendcustom strings to payloads for filter bypass.
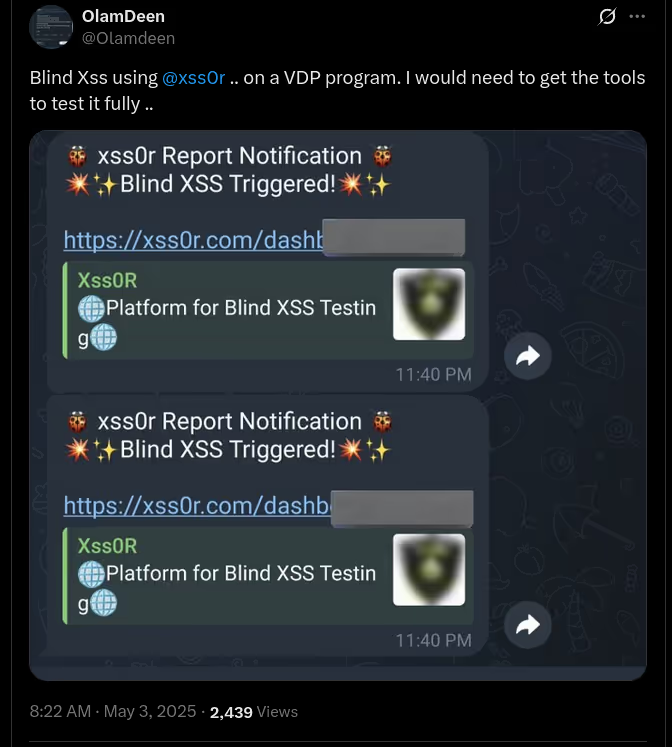
✅ Blindusername:
Inject your xss0r.comusername into User-Agent for BlindXSS tracking.
✅ Spray (BlindXSS):
BlindXSS spraying todiscover stored and deferred vulnerabilities.
✅ Crawler:
Crawl internal links deeply,expanding attack surface automatically.
✅ Fuzzer:
Fuzz inputs to see whatcharacters are blocked, filtered, or encoded.
✅ Clickme:
Simulate mouse clicks andkeyboard actions to trigger DOM-based payloads.
✅ Limit:
Control requests per minute toavoid WAFs or rate limits.
✅ Save / Resume:
Save scan progress andresume it later without data loss.
✅ CRLF Injection:
Scan for CRLF injectionflaws on subdomains or query parameters.
✅ Inspector:
Advanced passive & activeinspection for hidden endpoints.
✅ Stealth:
Low / Medium / High stealthmodes to evade detection by advanced WAFs.
✅ All Mode:
Run combined path and queryscanning in one optimized execution.
✅ Fullscan:
Force execution of the entirepayload library for exhaustive testing.
✅ Threads:
Listed as n/a,typically means dynamically scales for enterprise workloads.
✅ Payloads:
Handles large or dynamicpayload sets (n/a).
⚠ License Details:
• License: 1 User
•Devices: Supports up to 4 devices on 2 different IP addresses
🏢 BUSINESS PLAN Enterprise Advantages:
•Comes with 2 additional gratis licenses (total 3 seats) so multipleteam members can run tests simultaneously.
• Supports up to 10devices, regardless of location or IP address — ideal fordistributed or multi-office teams.
• Includes priority 24/7live chat support, ensuring expert help whenever your team needs it.